What makes a Vulnerability Assessment by ISE effective?
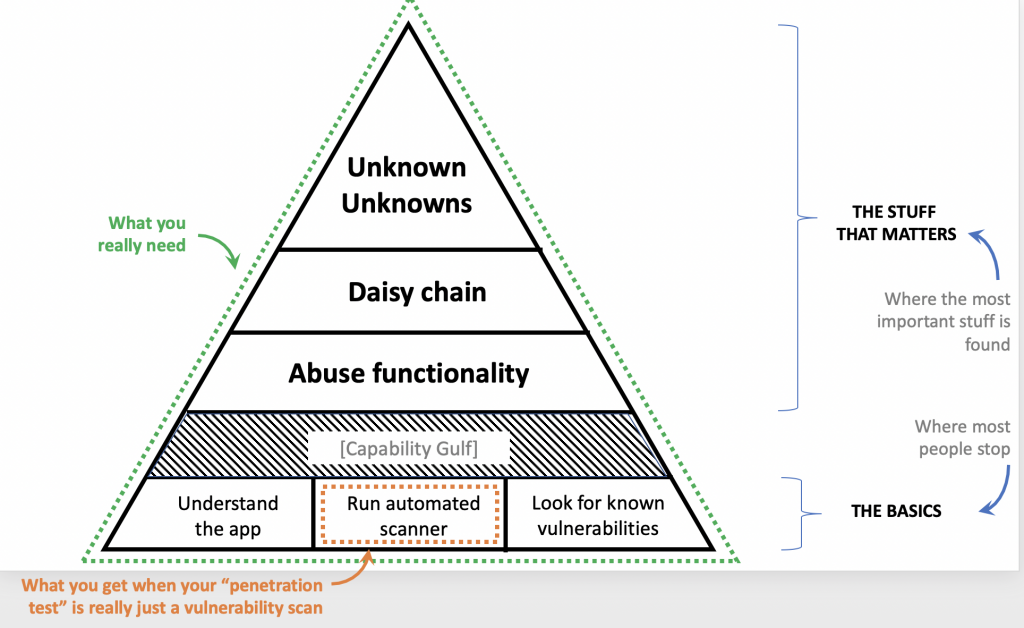
Commodity approaches to security often rely solely on tool automation. These are cheap and quick, but barely scratch the surface. Many don’t even consider how the system works at all, because they don’t need to. Most look only for known vulnerabilities.
That’s where commodity approaches to security stop. Yet, the more important vulnerabilities are never found at this basic level of effort.
You must go past the basics to find your most important vulnerabilities.
The 0-days, the custom exploits, and the unknown unknowns all require a higher level of effort and expertise. They require intuition, manual investigation, and an attacker mindset.
If you have important assets to protect, this is the level you want. Our customers all are in that category, and see great value in thorough, manual, vulnerability assessment.
Contact us to find out if a vulnerability assessment is right for you, too.